Introduction To Encryption: How It Works And Why It's Important
Introduction
The internet is open. If you don't know, then yes! It's like shouting in a crowd. Everyone can hear you. If you call out to a friend, everyone else within range will hear. Some people might walk past, but others will probably watch you. If they do get interested, it could lead to unwanted attention. In today's open society, we are paranoid. We believe in being innocent until proven guilty, but there are other beliefs that contradict this. Some people think it's better to prevent something from happening than to try to fix it afterwards. Others believe that once something's been done, it can't be undone. These ideas make people think twice before they trust other people.
If you call your friend and want them to hear and understand you, you have to use a way of speaking that only you and they know. This can be anything, like a change in voice tone or shouting at a particular frequency. We can say that they encrypt the call, and the method they use is called encryption.
What Is Encryption
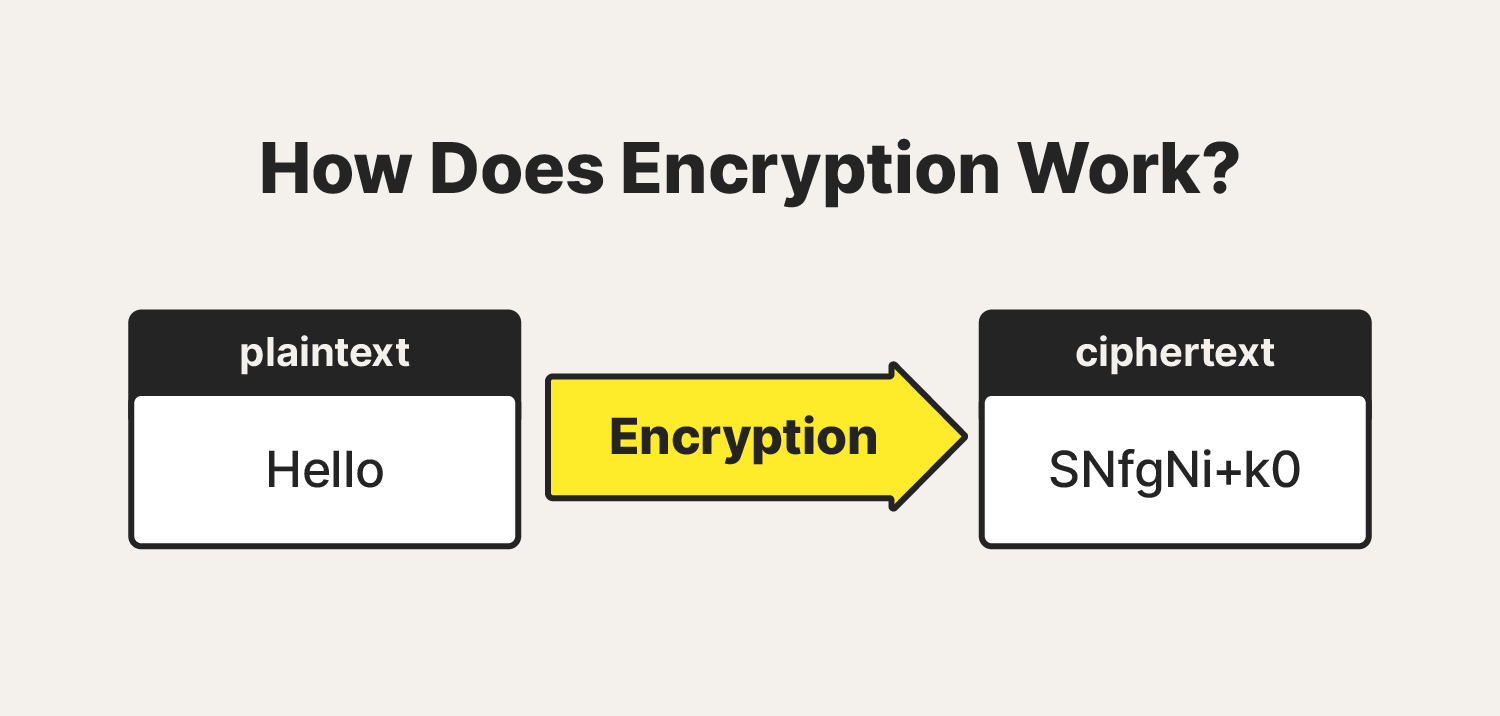
In technology, encryption is the process of turning plain text into cipher text, which is unreadable without the right key. This makes sure that only authorized people can access the information. The word 'encryption' is not new. People have been using it for centuries. Now, in the digital age, modern cryptographic algorithms are used instead of old-fashioned human decrypted cipher texts.
Types of Encryptions
There are two kinds of encryption used in the modern world. If you use a digital device, you should know about them.
They are:
- Symmetric Encryption
- Asymmetric Encryption
Symmetric Encryption uses a single key for both encryption and decryption. Advanced Encryption Standard (AES) and Data Encryption Standard (DES) are some implementations of symmetric encryption.
Let us try to understand it by considering an illustration:
Let's encrypt the plain text "HELLO." Let's use the alphabet for encryption. Moving the letters by two gives us JGNNQ. The recipient needs to know the logic to decode it. We'll call this (logic) the key. Once they know the key, they can decode JGNNQ to get HELLO.
The key can be leaked, so it's important to share it only with the intended recipient.
It is said to be symmetric because there is only one key involved and is shared among both the parties.
The advantage of symmetric encryption is it is faster, efficient and less resource intensive for large volumes of data.
How it is actually embedded in your daily life is when you used a password all the times on the internet, to log in to your computer where when you enter the password you are actually unlocking the contents on your hard drive. If someone tries to view the contents of a password-protected hard drive, they will only see jumbled text.
Yes, password protected encryption, or key protected encryption is not only used as a method of validation of identity but also is a type of symmetric encryption which is used to encrypt your data. It depends on the company and its policy in which way to do they want the encryption to be used.
Some common symmetric encryption algorithms are Advanced Encryption Standard (AES), Data Encryption Standard (DES), Triple Data Encryption Standard (3DES), Blowfish and TwoFish. Of which AES gained recognition and was quickly dominantly adapted and was also deemed as the standard by NIST while the others were deemed obsolete by today's current standards of average processing power of a machine.
Three practical symmetric encryption examples:
-
Secure messaging apps (e.g., WhatsApp, Signal): These messaging platforms use symmetric encryption, such as the Signal Protocol, to ensure that messages are encrypted end-to-end, allowing only the intended recipients to read the content.
-
File encryption software (e.g., VeraCrypt, AxCrypt): Symmetric encryption algorithms like AES are employed by file encryption software to protect sensitive data stored on devices, ensuring data remains secure even if the device is lost or stolen.
- BitLocker: When you activate BitLocker on a Windows computer to encrypt all hard drives. By unlocking the PC with his/her passcode, the user will decrypt data without the risk of exposing its secret encryption key.
A simple illustration about the working of asymmetric encryption is as follows and also get used to the term "key" as the frequency of its occurrence will be a lot.
If there are two persons exchanging data and want their communication to be secure for which each of them will generate a pair of keys.
The term key in this context is a string (single sentence) of certain length containing random letters which is then included by an algorithm or any methodology used to convert the plain text into cipher text or vice-versa.
Now, both parties each have a pair of unique keys. The keys in a pair are termed 'public key' and 'private key'. Now, the public key is shared among others and is made available to the public whereas the private key is kept private and not shared with anyone.
It will all make sense now, just follow along...The public and private key pair that a user has are considered to be the broken pieces of one single key and so when they are joined again, they become a complete key which can then be used for unlocking or decrypting. And also, either of the public key or private key cannot be replicated which means they are only one in the entire world.
So, the sender uses the public key of the recipient in an algorithm that converts the plain text into cipher text which can only be decrypted with the help of correlating private key of the recipient. As the keys are both unique and there can only be one public key and private key pair and with the private key always being at the recipient, no other individual who intercepts the communication can convert the cipher text back to plain text.
So, summarizing the data encrypted with one half of the key (public key) can only be decrypted its correlating other half of the key (private key) and vice-versa.
Please follow through a visualization tutorial here for better grasping.
Some common algorithms that implement asymmetric encryption are RSA, Diffie-Hellman, Elliptic Curve Cryptography (ECC).
Three practical asymmetric encryption examples:
-
Secure email communications (e.g., PGP, S/MIME): Asymmetric encryption is utilized in secure email communication protocols such as Pretty Good Privacy (PGP) and Secure/Multipurpose Internet Mail Extensions (S/MIME). These protocols leverage public and private keys to encrypt email content, ensuring only the intended recipient with the correct private key can decrypt and read the message. This method provides confidentiality and maintains message integrity.
-
Digital signatures for document authenticity and integrity (e.g., Adobe Sign, DocuSign): Asymmetric encryption is also used in digital signature services like Adobe Sign and DocuSign. When a user signs a document digitally, their private key is used to create a unique signature. The recipient can then verify the authenticity and integrity of the document using the sender's public key. This process ensures the document hasn't been tampered with and confirms the identity of the signer.
- Secure key exchange and establishment in SSL/TLS protocol for secure websites: Asymmetric encryption plays a vital role in the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, which are used to secure data transmission between a user's browser and a website. During the initial handshake process, asymmetric encryption is used for the secure exchange of a symmetric encryption key, which is then used to encrypt and decrypt data for the remainder of the session. This approach combines the security advantages of asymmetric encryption with the speed of symmetric encryption for efficient and secure communication.
Real-World Applications of Encryption
I think you can by now illustrate by yourself some of the applications. But let's list out some generic and targeted applications
- Data Protection: Encryption secures data both in transit (e.g., HTTPS for secure web browsing) and at rest (e.g., encrypted storage devices).
- Messaging Apps: End-to-end encryption ensures that only the communicating users can read the messages (e.g., WhatsApp, Signal).
- Virtual Private Networks (VPNs): VPNs encrypt internet traffic to protect users' privacy and security online.
-
File encryption: Symmetric encryption is
preferred for encrypting files due to its speed and computational
efficiency, making it ideal for handling large volumes of data.
- Secure key exchange: Asymmetric encryption is commonly used for secure key exchange in protocols like SSL/TLS, ensuring that symmetric keys can be safely shared between parties without being intercepted.
- Digital signatures: Asymmetric encryption is suitable for creating digital signatures, allowing users to authenticate documents and verify their integrity using public and private key pairs.
Importance of Encryption in Protecting Data and Privacy
- Preventing Unauthorized Access: Ensuring that only authorized users can access the encrypted data.
- Mitigating Data Breaches: Reducing the impact of data breaches by making stolen data unreadable
- Integrity and Credibility: To prove the source of the sender if required and that the message even if intercepted remain untampered.
Common Encryption Algorithms and Their Use Cases
(Yes, cryptography is built on top of mathematics!).
AES (Symmetric)
AES is one of the most frequently used algorithms. It is fast, with a
variable key length option that gives it extra security. It is ideal when
handling large amounts of encrypted data.
Explanation:
TwoFish (Symmetric - previously BlowFish)
The main attraction of TwoFish is its flexibility in performance, giving you total control of the encryption speed.
Explanation:
- paper-twofish-paper.pdf (schneier.com)
- Academic: The Twofish Encryption Algorithm - Schneier on Security
- Schneier on Security: Twofish
3DES (Symmetric)
Explanation:
- Academic paper including explanation of Des and 3Des
- What is 3DES encryption and how does DES work? | Comparitech
RSA (Asymmetric)
Since its speed isn’t convenient for processing large amounts of data, RSA encryption is mostly used in digital signatures, email encryption, SSL/TLS certificates, and browsers.
Explanation:
- What is RSA encryption and how does it work? (comparitech.com)
- Academic paper for factorization of RSA
ECC (Asymmetric)
The low-cost, low-impact, high-security combination makes it the ideal standard for protecting sensitive mobiles and apps. It may likely be the algorithm of the future.
Explanation:
Blowing Off Encryption
Some people use encryption to hide their messages, but this can also be used for bad purposes.
Pavel Durov, the CEO of Telegram, was arrested in France on 25 August 2024 for supporting user privacy over the platform's lack of moderation on child sex abuse.
Security teams want to track what's being sent on these apps, so they ask companies to share users' private keys. If these keys are leaked, everyone on the app could be at risk.
Another way for government agencies to access private messages is for the developers to create a vulnerability that the agencies can then exploit to monitor the content. But there is a risk that this vulnerability could be discovered and exploited by hackers or malicious actors.
This highlights the ever-present and ongoing conflict between personal privacy and national security.
Related Articles (2023 - 2015):
- The fight over the future of encryption, explained | MIT Technology Review
- The NSA Swears It Has ‘No Backdoors’ in Next-Gen Encryption | WIRED
- A Digital Dystopia: How Calls for Backdoors to Encryption Would Ruin the Internet for Everyone - Internet Society
- US Department of Justice push for encryption backdoors might run afoul of First Amendment | CSO Online
- The backdoor threat to encryption (brookings.edu)
- It's Time to End the “Debate” on Encryption Backdoors (justsecurity.org)
Challenges and Future of Encryption
Despite its benefits, encryption faces several challenges which if simply put are
- Key Management: Securely generating, distributing, and storing encryption keys.
- Computational Overhead: The processing power required for encryption and decryption.
- Emerging Technologies: The advent of quantum computing poses a threat to current encryption methods, leading to the development of quantum-resistant algorithms.
Conclusion
The only things mentioned in the explanations were 'encryption by apps', 'platforms managing security' and 'enterprises managing data'. You trust them with your data, right? Why? They make policies and you expect them to follow them. If you don't take care of your data, corporations will take advantage of you. You decide what to do with your data. Only share it with people you trust. Your chats should be private. They should not be monitored or listened to. End of story.
Yes, you can't always control how data is shared online. To do so, you need to understand how the internet and browsers work, as well as encryption.
But you can take back control of your emails and messages. You can't control how emails are delivered, but you can choose what's in them. Look into encrypting your emails. This is important because sometimes you're not communicating publicly, just with one person. Make sure you both secure your conversation, respect each other's privacy and be patient with each other. Don't let comfort ruin your privacy. Start with the resources listed in the references section below.
References
- A New Approach of Cryptography for Data Encryption and Decryption | IEEE Conference Publication | IEEE Xplore
- Cryptographic Standards and Guidelines | CSRC (nist.gov)
- Encryption by prey project
- https://us.norton.com/blog/privacy/what-is-encryption
- https://www.practicalnetworking.net/series/cryptography/cryptography/
- https://theunlockr.com/what-is-encryption/
Recommendations
Stay secure!
Wishing you a good privacy!
As always,
Venu Kotamraju ;-)



.png)
Though I have studied these in my undergrad, it was great looking back into things again and also cleared some gaps in my knowledge.
ReplyDeleteGood to know Varun. However, this particular topic requires an exposure of practical implementation too as the motivation behind writing this is to get people to apply it. Due to the nature of the concept, the content was already at its length, and I was tied down to include only the theoretical explanation. But I will come back with another part for this post by which as a reference you start doing encryption in your day life. And make sure you do! Until then the research is your own to conduct and do not forget the Recommendations section...!
Delete